theHarvester is a tool for gathering e-mail accounts, sub-domain names, virtual hosts, open ports/ banners, and employee names from different public sources (search engines, pgp key servers).
The sources supported are:
Google – emails, subdomains/hostnames
Google profiles – Employee names
Bing search – emails, subdomains/hostnames, virtual hosts
Pgp servers – emails, subdomains/hostnames
LinkedIn – Employee names
Exalead – emails, subdomain/hostnames
To get started, if theHarvester is not available in your Linux distribution, go and download it from here or check the latest version from here.
Migrate to download directory and extract the file
➜ ~ cd /home/james/Downloads ➜ ~ tar -xvzf theHarvester-2.2a.tar.gz
Migrate to extracted directory and provide execute permission to the theHarvester.py
➜ ~ cd theHarvester-2.2a/ ➜ ~ chmod 755 theHarvester.py
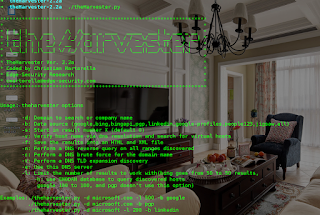
After getting in to that, simply run ./theHarvester.py , it will display version and other option that can be used with this tool with detailed description as seen on the diagram below,
To use the tool, use the following syntax
➜ ~ ./theHarvester.py -d [domainname] -l 300 -b [search engine name]
Example;
-The command below will search all email addresses, sub-domains,, virtual hosts found any where in google.
➜ ~ ./theHarvester.py -d facebook.com -l 300 -b google
-The command below will search email address, sub-domains, virtual hosts etc of microsoft.com domain found in most search engines.
➜ ~ ./theHarvester.py -d microsoft.com -l 300 -b all
If you are using KaliLinux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments the tool comes pre-installed.
This tool is designed to help the penetration tester on an earlier stage; it is an effective, simple and easy to use, so don't abuse it, if you use it for hacking, hack ethically.
Enjoy!!

No comments:
Post a Comment