If you are working in organization which uses Dropbox at the daily bases, you might came across with bandwidth issue especially when syncing large file across different computers. At normal the file should be uploaded to Dropbox servers and then downloaded to each individual computers where the file is shared and this is considerable large use of bandwidth and takes time especially if the file is large enough, but with Dropbox LAN syncing feature bandwidth can be saved and syncing time can be minimized.
What is Dropbox LAN sync?
Dropbox LAN Sync is a feature that allows you to download files from other computers on your network, saving time and bandwidth compared to downloading them from Dropbox servers.
The LAN Sync feature can speed up the syncing of files that exist on your local area network (shared folders and computers connected to the network). It allows Dropbox to check for new versions of a file on your network without having to download the copy of the latter from Dropbox servers.
What is Dropbox LAN sync prerequisites?
If you want to force a LAN Sync, you’ll need two computers on the network with either the same account or a shared folder in common. Add a file to one of the computers, and the other computer should attempt a LAN Sync. The computers should be in the same LAN.
How to configure and enable LAN sync?
a. Install the Dropbox client on your PC: www.dropbox.com.
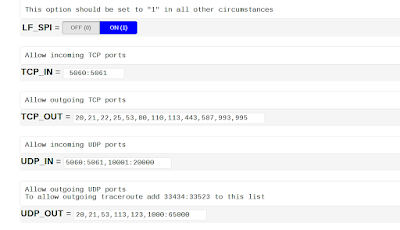
b. Allow Dropbox.exe in your firewall's settings: The LAN Sync feature requires access to port 17500 (TCP). Go to the Control Panel > Firewall > Allow app or feature through Windows Firewall.
c. Click on the Dropbox tray icon > Preferences. Go to the Bandwidth tab and tick the Enable LAN sync checkbox: Click on Apply > OK.
Enjoy!
What is Dropbox LAN sync?
Dropbox LAN Sync is a feature that allows you to download files from other computers on your network, saving time and bandwidth compared to downloading them from Dropbox servers.
The LAN Sync feature can speed up the syncing of files that exist on your local area network (shared folders and computers connected to the network). It allows Dropbox to check for new versions of a file on your network without having to download the copy of the latter from Dropbox servers.
What is Dropbox LAN sync prerequisites?
If you want to force a LAN Sync, you’ll need two computers on the network with either the same account or a shared folder in common. Add a file to one of the computers, and the other computer should attempt a LAN Sync. The computers should be in the same LAN.
How to configure and enable LAN sync?
a. Install the Dropbox client on your PC: www.dropbox.com.
b. Allow Dropbox.exe in your firewall's settings: The LAN Sync feature requires access to port 17500 (TCP). Go to the Control Panel > Firewall > Allow app or feature through Windows Firewall.
c. Click on the Dropbox tray icon > Preferences. Go to the Bandwidth tab and tick the Enable LAN sync checkbox: Click on Apply > OK.
Enjoy!